OPORA appealed to the European Solidarity party for e-mails that allegedly involve its communication with the Security Service of Ukraine (SBU), which were mentioned by public sources on 9 October. Having received the data, OPORA asked two independent organizations, particularly the Digital Security Lab (Ukraine) and the International Centre for Defence and Security(Estonia), for an expert assessment. They both gave opinions that confirm that Russian-origin offenders imitated the correspondence containing illegal demands from the SBU addressed to the European Solidarity party.
In fact, it was a provocation aimed to publicly discredit the SBU, as well as to cause public confrontation between electoral subjects and Ukrainian authorities. The revealed fact is a probable evidence of Russia's interference in the election process in Ukraine. Thus, OPORA calls on the Security Service of Ukraine and the Cyber Police Department to investigate this incident and determine the origin of this letter and its sender, besides making public statements.
On 9 October 2020, Civil Network OPORA learned on a Facebook page of MP Herashchenko Iryna Volodymyrivna about a written appeal #26/2/4/4-3245 of 1 October 2020 to the European Solidarity party, which is in opposition, from the so-called Main Directorate of the Security Service of Ukraine in Donetsk and Luhansk oblasts. The document, published online at the request of OPORA, contained request for a list of party's candidates to city, village, settlement and raion councils, as well as village, settlement, city heads in Donetsk and Luhansk oblasts, brief information about them, detailed biographies, information about their campaign expenses, etc. OPORA assessed such remands as excessive, illegal, and clearly absurd for a number of reasons. At the same time, a request to the opposition party, whose leader, the fifth President of Ukraine Petro Poroshenko, was publicly known to be in hospital with COVID-19, looked like a provocation to a public emotional reaction, but not a data request.
This request is not a typical information request from a public authority during an official election campaign. The Election Code establishes a list of rights and responsibilities of electoral subjects, as well as powers, limits and ways of their exercise. Besides that, the document contains wording and addressing that are not typical for Ukrainian paperwork, as well as illegal demands, errors and data inaccuracies.
Despite on 9 October 2020 the SBU had disproved on its website the sending of letter dated 1 October (#26/2/4/4-3245), this incident has gained a strong public response and, therefore, requires a legal and public assessment. Thus, Civil Network OPORA, as an organization that monitors the 2020 local elections, asked the Head of Central Board of the European Solidarity party for the necessary data of e-mailing to make an analysis.
Both the abuse of enforcement administrative resource and the interference of third parties, such as the Russian Federation, in the electoral process, aimed to disinformation and manipulate, are global challenges for the election process.
The public information, published online, one can see that the letter was sent from e-mail [email protected]. However, according to the SBU website, e-mail address of the State Security Service of Ukraine in Donetsk and Luhansk oblasts is [email protected]. However, despite the addresses do not match, the party received the letter from the SBU's domain (ssu.gov.ua), what is definitely alerting. However, there are many ways to forge an email sender nowadays (Email spoofing), which are often used by cyber criminals or intelligence agencies of foreign states. To identify a real domain of this letter, as well as to potentially find out the IP address, from which the letter was sent, and to verify the authenticity of the letter, OPORA received an .eml (.emlx, .msg) file of the letter.
The From: field contains the e-mail address osbu_don@ssu[.]gov[.]ua, imitating the official domain name of the Security Service of Ukraine. However, the real e-mail address of the sender was 1504191355@lenta[.]ru, using a free mailing service rambler[.]ru.
IP-address of the sender was Kyiv 176 [.]107[.]185[.]28, what may mean that the user leased a proxy server with PHPMailer 5.2.26 mail client installed, from where this server was managed.
The PDF-file itself was created using a very old version of Office Word 10, what may mean that a virtual machine or unsatisfactory software was used.
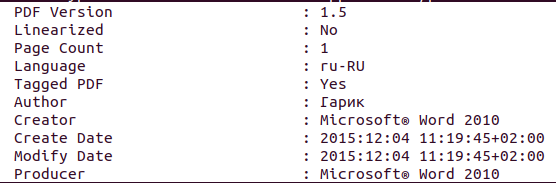
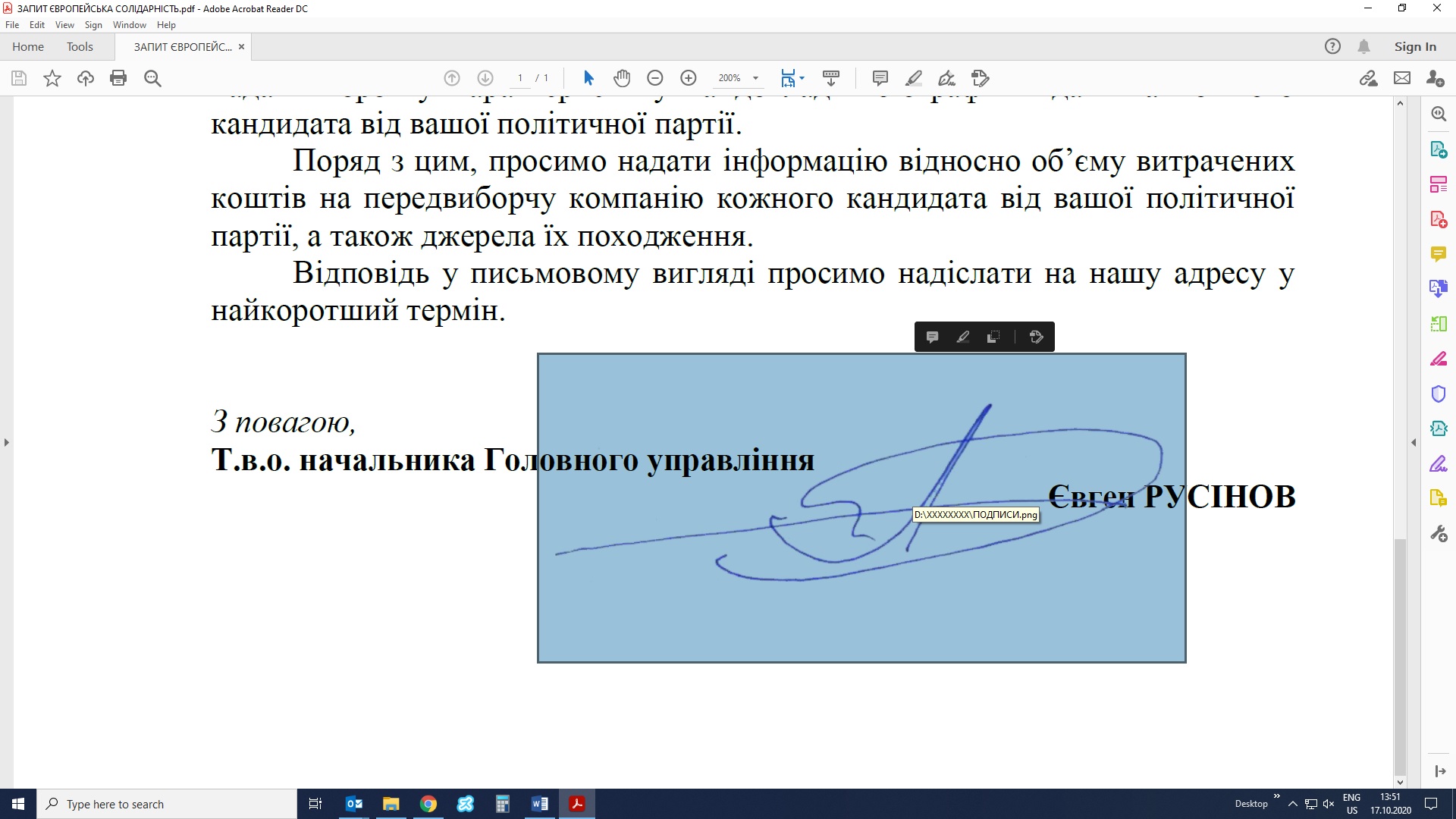
The file contains several images, including the state emblem, a handwritten signature and dates. Metadata of images show that original image files on the user's computer were named in Russian.
Metadata of images:
D:\load-gerb-ukrainy копия111111син.png
D:\XXXXXXXX\ПОДПИСИ.png
D:\XXXXXXXX\ДАТЫ21.png
D:\XXXXXXXX\3245.png
D:\XXXXXXXX\ДАТЫ211.png
We can not tell for sure who had initiated this provocation, but the Security Service of Ukraine should not only give a public response to it, like the one on its website mentioning it didn't send such a letter, but also investigate the situation and identify the offenders or their origin.
Democracy is extremely vulnerable, as long as various forms of democracy work perfectly only providing that everyone adheres to the law or international standards. Thus, a race must be competitive, a winner must get the result via a fair vote count, and each election participant must form a political position free from pressure, threats, intimidation and fraud. Intervention of the Russian Federation is not a single-time issue. However, it's difficult to prove it, as it usually happens in a non-public manner: information attacks with fake materials triggering emotions of the people, activities of agents of influence, shadow finances. These facts need proper investigation and response. Besides that, Ukrainian institutions should cooperate to prevent any illegal interference in the election. We also call on political parties and candidates to thoroughly investigate into suspicious incidents before making any public allegations against the public authorities and political rivals. It is also important to educate citizens about cyber hygiene and how to verify data obtained from third parties.
